Hardware Root of Trust protection
As the Internet of Things (IoT) and embedded devices become more connected and widespread, securing them from the ground up is critical. A Hardware Root of Trust provides the essential foundation for device security, anchoring all cryptographic operations in a secure, tamper-resistant environment.
Public Key Infrastructure (PKI) is widely recognized in the IT industry as the ideal framework for combining strong security with operational flexibility. By integrating PKI, MULTOS technology delivers a cost-effective and adaptable hardware root of trust for IoT and embedded devices.
The robust MULTOS operating system, featuring an ultra-secure execution environment, works seamlessly with tamper-resistant microcontrollers to deliver complete security solutions—whether used as standalone cryptographic co-processors or as the device’s main secure microcontroller.
As shown in the short video below, MULTOS protects against malware threats, secures data, enables safe over-the-air updates during the device lifecycle, and easily scales to support large, complex deployments.

Protecting Device Software
MULTOS is implemented within hardened micro-controllers with secure functions such as power scrambling, internal data encryption, and advanced error detection, which offer significantly better protection than a software based approach.
With MULTOS the robust operating system within a hardened micro-controller adds not only security but also functionality by supporting an on-board secure execution environment to essentially police sensitive cryptographic operations. MULTOS can be used to store sensitive data such as keys and device credentials, critical for authentication processes, can be used to protect the boot-up processes of other device processors, and has its own secure boot up process. Many IoT devices require software updates over their lifecycle, so implementing MULTOS is a robust way to ensure only authorised updates are accepted.
Securing Device Identity & Authentication
Devices can have their ID changed or duplicated to facilitate fraud, and authentication processes can be interfered with to cause a variety problems.
A hardened micro-controller can have a unique Identity and strong cryptographic credentials loaded and securely stored, ensuring the device cannot be easily cloned. MULTOS uses asymmetric key pairs (matched sets containing public and private keys) which are generated and loaded into the mirco-controller to provide the endpoint with a strong personalised identity. The MULTOS Carrier Device (MCD) ID number is generated and linked with a specific device owner ID number and the PKI key set to form the complete robust unique identity. The latest MULTOS specifications support strong PKI cryptographic algorithms with extended key lengths.

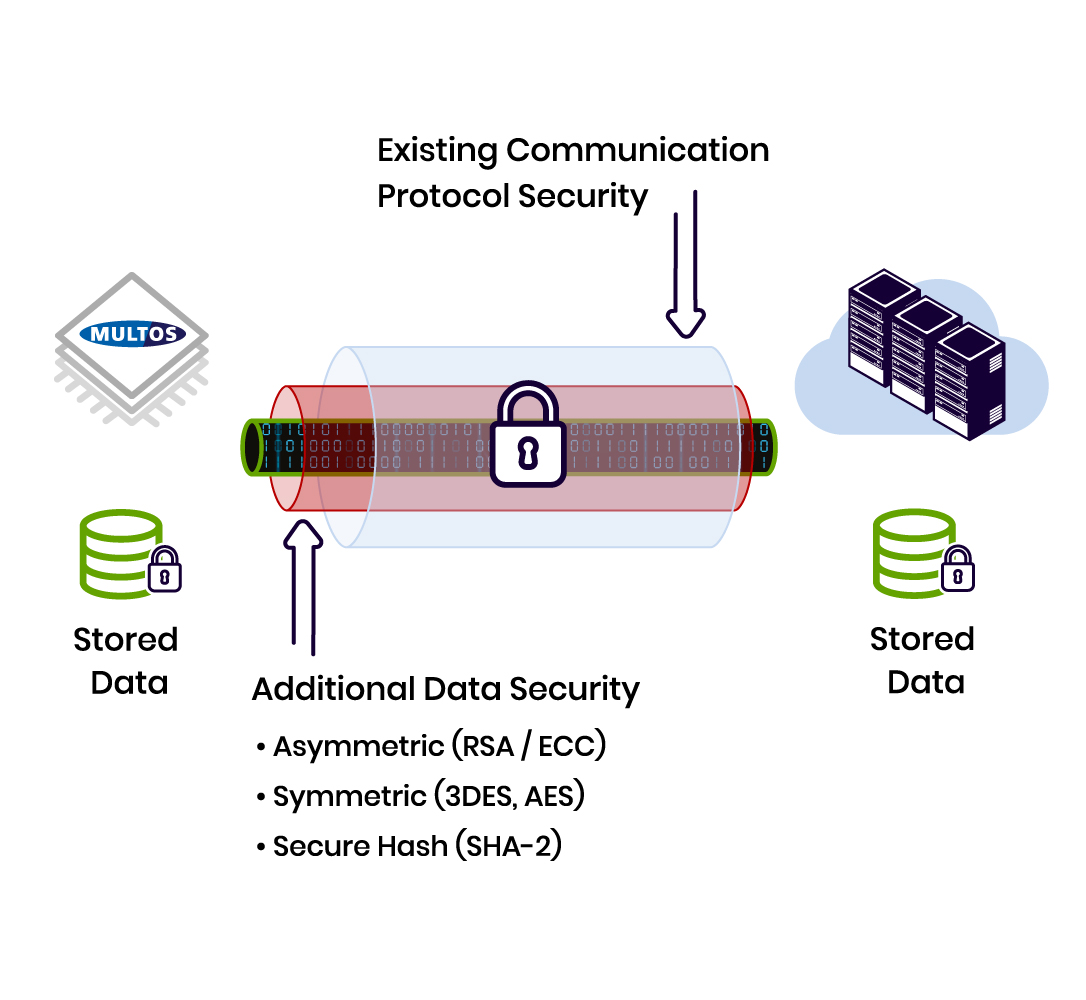
Also enforcing strong device and system mutual authentication based on secure hardware protected credentials can provide a robust implementation to defend against attacks.
Many common communication and authentication protocols do have security built in, but often these can be improved.
Implementing a hardware RoT with securely stored additional encryption keys, allows an additional layer of protection to be applied for critical data.
MULTOS is a security micro-controller which can be customised to add such additional protection.
Secure Device Provisioning & Lifecycle
Full consideration of the lifecycle of any connected device should feature highly with solution providers. Some IoT devices could be in use for many years and most would benefit from a well-managed, flexible and controlled lifecycle. A device may need a number of remote functional updates to reconfigure or modify the service over time. Of course security updates are a likely requirement as attacks evolve and improve over time.
Device application and data provisioning requirements may vary depending on the service. Utilising a strong key management method can provide the necessary simplification and security required for a robust provisioning solution. MULTOS uses asymmetric cryptography for managing the deployment of the device, and utilises a secure packet to deploy the device content. The use of secure, encrypted load packets between the device and the host can simplify and reduce key management.


The use of asymmetric cryptography easily allows the MULTOS device to be managed by the device owner, whilst any third party businesses can load their content to the device assuming the owner has authorised the change.
Any third party sensitive content can be encrypted such that the owner and any unauthorised entity would not have access.
This versatile mechanism built into the MULTOS specifications is an efficient solution for the complex business models and allows firms to deliver their services on already issued infrastructure, potentially reducing costs and speed to market.
Flexibility
MULTOS is not just flexible from a lifecycle and loading mechanism perspective, and from an implementation perspective as a co-processor or main micro-controller, but also can be programmed and customised as required.
MULTOS has useful default functionality but is open for developers to modify and add security features as required.
MULTOS supporting SDKs reduce the design effort, offer online support and contain sample application software for integrating secure connectivity using TLS/DTLS 1.2 to widely used IoT platforms such as AWS IoT. Being programmable MULTOS can support many other IoT platform solutions and bespoke security protocols. The plug-in format variant allows convenient integration with RasberryPi® and Arduino® single-board computers.

The MULTOS Coffee Machine Demo

A MULTOS smart card making use of Elliptic Curve Cryptography for authentication
PLAYConnected Device Security

A Ready-Made Secure IoT Environment
Click hereBuy IoT Developer Kit

Available from Universal Smart Cards
Click here